Fear of adopting EMR: Is it for good reason?
Are you worried about LULZSec or Anonymous hacking the Cloud and going after your health information?
You really shouldn’t be.
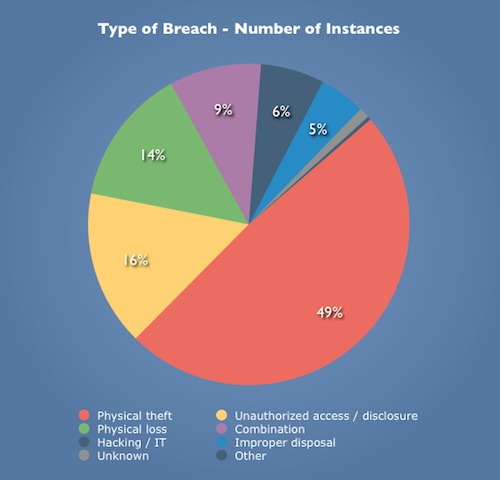
As demonstrated by “The Wall of Shame” pie chart illustrated below, almost 50% of the security breaches are due to carelessness. Michael Koploy states: “Overall, physical theft and loss accounted for about 63% of the reported breaches. Unauthorized access / disclosure accounted for another 16%, while hacking was only 6%.” As Koploy states, do you really think hackers would rather seek your HDL/LDL cholesterol count or a bank account. (Good point!)
- 6,800 paper records that were supposedly mailed but never received
- an impostor posing as a recycling-service employee stealing over 1,300 individuals’ records and films; and,
- a laptop stolen by a former employee that contained personal health records of over 50,000 patients.
Read more here.
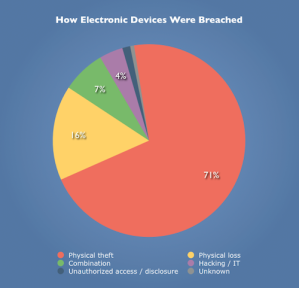
Once you realize how so many of these security breaches could have been avoided combined with the realization that doctors also love their mobile computers/laptops/smartphones, the statistics of security breaches become very real. There are 10,000 mobile health care apps that allow users to access EMRs and according to Mobile Marketing Watch, one in three doctors own an iPad, and another 28% are planning on buying one within the next six months. Within the past two year there have been 116 data breaches of over 500 records due to the theft or loss of mobile devices. We really need to have more stringent safe guards, not only training of the health care professionals, but as the FCC and FDA work together as the convergence of technologies deal with new health care apps there needs to be better protection for the consumers. The Wall of Shame isn’t going to disappear unless the government and the people come to terms with their health care records being exposed.
Here are 8 tactics for mobile data privacy & security (via Mary Mosquera of GovHealthIT )
1. Don’t store sensitive data on wireless devices. If required, encrypt data.
2. Enable password protection on wireless devices and configure the lock screen to come on after a short period of inactivity.
3. Turn on the “remote wipe” feature of wireless devices.
4. Enable Wi-Fi network security. Do not use wired equivalent privacy (WEP). Wi-Fi protected access (WPA-1) with strong passphrases offers better security. Use WPA-2 if possible.
5. Change the default service set identifier (SSID) and administrative passwords.
6. Don’t transmit your wireless router’s SSID.
7. Only allow devices to connect by specifying their hardware media access control (MAC) address.
8. Establish a wireless intrusion prevention system.